Table of Contents
The Internet of Things brings us closer to the exciting parts and aspects of cyberpunk movies. Anyone can now be the person who turns on the coffee maker remotely with one press of the button, then puts on a smartwatch to check their heart rate, and then drives to work when the office is managed by smart technologies. And feel like real-life Tony Stark, at least in part.
IoT is present in almost every part of our life: smart homes, smart manufacturing, smart hospitals, smart cities… Connected things grant us more opportunities for automation and remote operations, but there is a flip side to this story. Are we sure that IoT doesn’t expose our privacy and safety?
Unfortunately, IoT devices are prone to cyberattacks. Security isn’t their strongest feature, and a large number of manufacturers don’t put a lot of emphasis on it, neglecting to take care of it. As a result, dozens of IoT devices enter the market already predisposed to being compromised.
The impact of such weak measures can be detrimental: hackers can easily access our personal and financial data, they can spy on our houses, offices, and other work premises, or altogether block operations of major enterprises and public services.
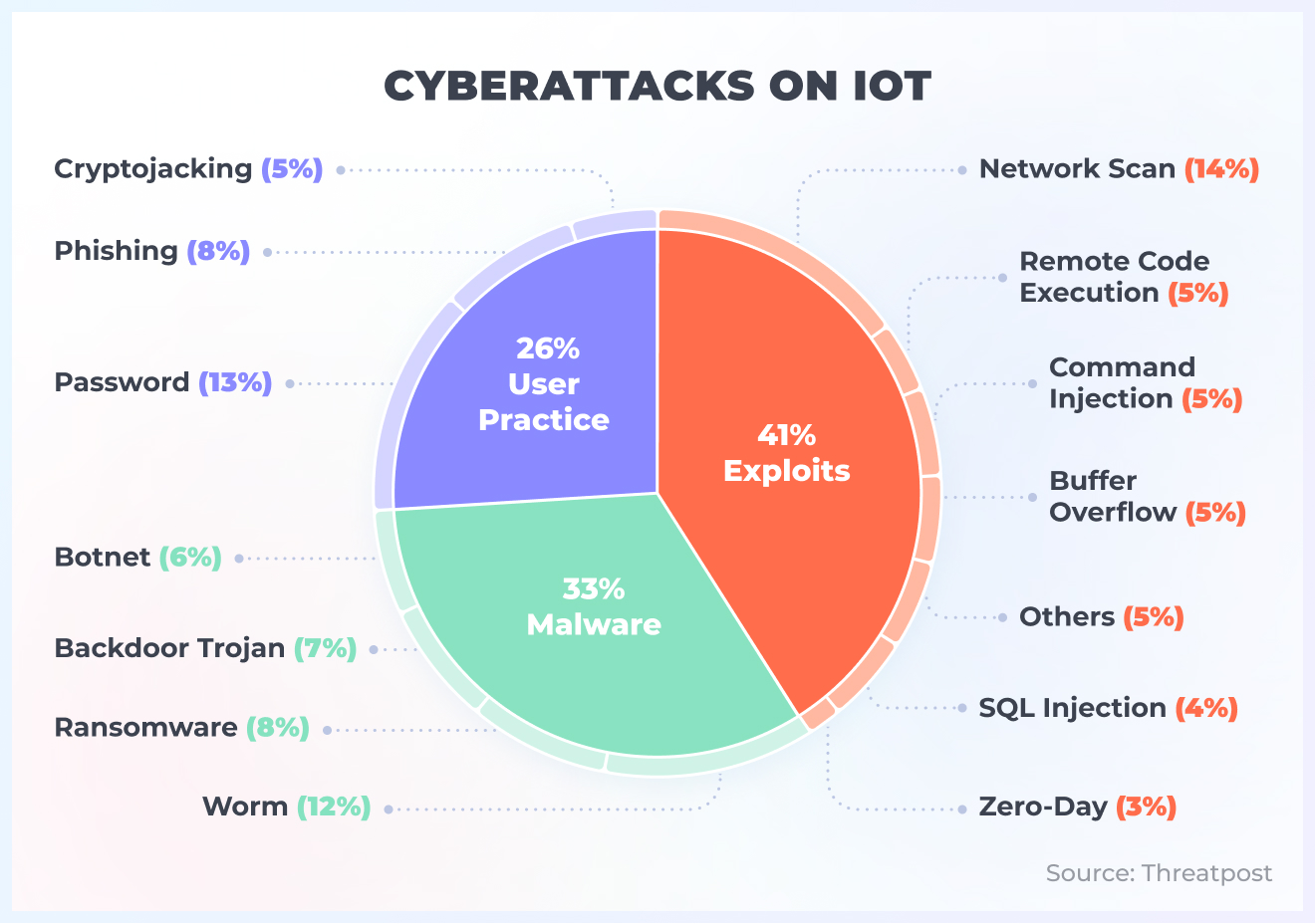
However, we firmly believe that even with these considerable concerns, IoT technologies are by far worth it and should be implemented. But strong safety strategy is required, and with this article, we will guide you through the main aspects of IoT cybersecurity.
Types of IoT Security Attacks
Unprotected IoT devices put your whole IT system at risk. So, to mitigate the possible risks, you need to be prepared ahead of time for any complications that might arise.
Unauthorized access to devices
The biggest concern is that without enough proper security measures in place, anyone can get control over your IoT devices. Ken Munro, an ethical hacker, explains how even simple IoT devices we use every day make us vulnerable.
Ken explains it on the example of smart home and kids toys, but let’s extrapolate it onto a more global context. In 2017, it was confirmed that St. Jude implantable cardiac devices can be hacked. Luckily, there were no such cases, no one was harmed and the company released a security patch quickly, but it only proves that there is a big chance that your IoT device may be remotely intercepted for control and used against your business.
Data leaks
Apart from the Internet of Things safety issues, there is also the question of privacy. IoT devices gather a lot of our personal information — for example, even a smart camera, say, in the office can reveal if you are not in the office, at home, etc.
And let’s not forget about IoT implemented in manufacturing or similar enterprises. Right now, companies are aiming for total connectivity to improve performance. Therefore, important databases, software, or computers are in danger of being compromised, especially in the case of a man-in-the-middle attack. So, one small neglected IoT sensor can lead to a global disaster for the whole business impacting so many actors.
Ransomware
Ransomware isn’t something new in the world of cybercrime — it’s a common attack that harms both citizens and businesses, no matter the size. But the logic behind ransomware attacks on IoT devices is slightly different.
IoT sensors usually don’t carry any data themselves, but if the intruders manage to hack sensors, they can lock up and disable them. Usually, it is possible to resolve the issue by resetting the device, but in some scenarios, it is inevitable that damage will be inflicted. For example, in January 2017, a hacker group managed to infect around 65% of surveillance cameras in Washington D.C just days ahead of Donald Trump’s presidential inauguration. As a result of this attack, cameras went offline for three days and caused people a great deal of anxiety.
Botnets
Cybercriminals have all the capacities to hijack IoT devices and use them for malicious purposes, like arranging DDoS attacks on other networks or mining cryptocurrency. Any botnet grows more powerful the higher the number of devices involved. In some cases, the destructive impact might be severe beyond belief, like we saw with the example of the Mirai botnet that managed to shut down a big part of the Internet.
Most Common Security Vulnerabilities in IoT Devices
IoT implementation brings a lot of danger to your internal system. According to The Ponemon Institute and Shared Assessments, 76% of risk professionals think that future cyberattacks will be done through IoT devices.
There are a lot of things you need to consider while implementing IoT into your business. Let’s consider them.
IT/OT convergence
In the past decades, there has always been a gap between IT and OT. Traditional OT systems weren’t connected to the Internet and were managed on-site. But the Internet of Things changed the traditional approaches, and now we encounter IT/OT convergence: OT, or systems that are used to monitor the performance of machinery and equipment, are enabled to IT, or basically to software that operates data flows.
This shift gives businesses new opportunities to optimize their processes and implement a higher level of automation. But such holistic connectivity may disrupt the whole production cycle and leave you with significant losses. And as you may have already guessed, the IoT device may become that entry point providing an easy entry barrier for intruders.
Lack of regular patch management
Patching is an efficient solution IoT manufacturers had come up with. When a new breach or vulnerability appears, they immediately focus on releasing a suitable patch that will neutralize the threat.
Though this strategy is commonly used to rectify security mistakes and gaps, it might not be as effective as in some cases. Firstly, hackers are usually a few steps ahead. They are dedicating all their attention to generating new, creatives ways to exploit security vulnerabilities in IoT devices, so even the latest patches or updates may be useless after they “work” on it for a couple of weeks.
Secondly, for some devices, like medical or industrial, it may be hard to implement regular updates due to specific regulations or difficulty accessing the devices themselves.
Insecure interfaces
Web, mobile, cloud, and API interfaces may become a weak link in your security. The majority of device vendors use authorization mechanisms that are common for the whole class of devices. Hence, interface protection falls on the shoulders of end-point users that aren’t especially skilled.
Insufficient data protection
As we established, IoT devices can be harmful elements that will jeopardize the security protection and privacy of confidential data. Unfortunately, it’s not only about the data which is stored on the devices — but it also concerns the whole network and other devices in it.
A lot of devices store data on the internal data carriers, so if intruders gain access remotely, they get to steal or even alter the data.
It’s extremely dangerous for IoT in manufacturing and healthcare domains. The integrity of medical devices can be thought of as synonymous with cardiac implants for heart patients – crucial, as any change of data may do significant harm to its user. At factories, IoT is usually connected to heavy machinery or robots. Corrupted data on this equipment might push people to make significant decisions that will destroy the machines and injure workers.
Poor IoT device management
Sloppy device management may lead to a security breach as well. Rogue devices may appear in your network, and if they remain unnoticed, it may lead to problems. The rogue device usually disguises itself as an existing device, but you have no access to it, while it subtly transfers the data to hackers or corrupts your storage.
The critical point here is to identify every device in your network, grant them unique names and keep track of them. Remember that expansive networks with a lot of similar IoT devices are a freebie for hackers.
Lack of Physical Hardening
It’s a very basic, but serious thread: if hackers steal your device, you are exposed. IoT devices are situated in different locations, rarely with day and night surveillance. Taking possession of any device, intruders may learn the capabilities of your network and improve their knowledge of the device models you use. All this info will highlight the possible weak sides of your environment and help the fraudsters infiltrate more easily.
The IoT Skills Gap
The adoption of IoT has accelerated even further and more than usual during the pandemic as companies started leaning on remote operations. However, it didn’t erase the issue of the skill gap, on the contrary, it exacerbated the problem.
What does the skill gap mean in the context of IoT? Well, IoT implementation and support require a wide set of skills from the person in charge: IoT information security, wireless network management, smart technology, coding, etc. It’s almost impossible to have such a person in your company if you have never worked with IoT before. At the same time, security or DevOps specialists may in turn also be lacking sufficient knowledge to successfully manage IoT networks.
But of course, there is a solution. Educational opportunities and focus on professional growth will help you become more aware of the trends. Meanwhile, we can help you create software applications for IoT sensors, test them on real devices and enhance the security of your interfaces.
Internet of Things Security Recommendations from Altamira Tech Team
Our development team has sufficient experience with software development for IoT. Some of our main success stories in this area of expertise are CTRL Golf and Aquiline Drones. Click on the links and check the details of the projects!
So, we decided to share our accumulated knowledge on IoT security, gathering suggestions on the most big-ticket items when it comes to security measures you need to take care of when deploying IoT into your IT ecosystem.
#1. Data channels
A lot of IoT devices use wireless data channels, like WiFi or Bluetooth without any data encryption. We suggest paying a lot of attention to encryption of:
- channels with the help of which devices communicate with the external environment;
- data with the help of X.509 or building your own VPN networks between devices and cloud services;
- clearly define the number of channels for the device; determine the necessary ones and exclude the rest. Channels here include not only networks but also interfaces: video processing, voice commands, IR signals, etc.
#2. Device access to common networks
If the device uses the Internet and is connected to the WiFi network or LAN cable through the router, it’s a possible vulnerability. We suggest:
- using mobile Internet, as the usage of SIM cards will isolate the device from the common network, but it will still have access to the web;
- using devices with a lot of computational power, so that it’s possible to implement a firewall on the device itself.
#3. Data storage on devices
Any IoT device can be a source of important and valuable data, and as we mentioned, it’s quite easy to gain access to it. To make this safe and save you from an ordeal, we suggest that you:
- encrypt data in local storage;
- implement access restriction to data when a physical connection to the storage occurs.
#4. Concerns related to users
Unfortunately, the mass production of IoT devices makes it so that we as users are in charge of ensuring that our devices are secure, protected and that only authorized parties access their results. Vendors release patches, but it’s the responsibility of users to install them. In case there are dozens of devices it’s challenging to control them all, especially when the average user doesn’t possess enough knowledge to manage even a few such devices.
So, here are some solutions we offer:
- implement authorization with unique accesses, for example, two-factor authentication through a cloud account or connecting a mobile application to the device via a unique QR code;
- enable remote updates;
- educational activities for end-point users inside your organization.
#5. Insufficient control of device operation by the vendor’s side
Unfortunately, a lot of security issues arise due to vendors’ production technologies, and lack of support after device enabling. We suggest:
- recording and saving device logs;
- regularly downloading encrypted and anonymized logs and their further processing by the vendor;
- regular diagnostics and elimination of possible issues.
In Conclusion
IoT is a worrisome area of IT in the eyes of many data specialists all over the world. The overarching reason — it’s widely adopted but still not nearly secure enough. We won’t deny the truth: IoT is the future, but its implementation should be wise, well thought out, and planned, otherwise, you risk endangering yourself to become an easy target for hackers.
But with sufficient attention and security procedures, you will be able to prevent possible threats and avoid security issues. Find our suggestions for the Internet of Things security useful? Feel free to share this article with your CTO!