Node.js, a cross-platform runtime environment, is generally secure. However, its reliance on numerous third-party packages, mainly open-source, poses some security concerns.
These packages are aggregated within the Node Package Manager (NPM) infrastructure, and a considerable portion may contain vulnerabilities, potentially compromising the security of the Node.js environment.
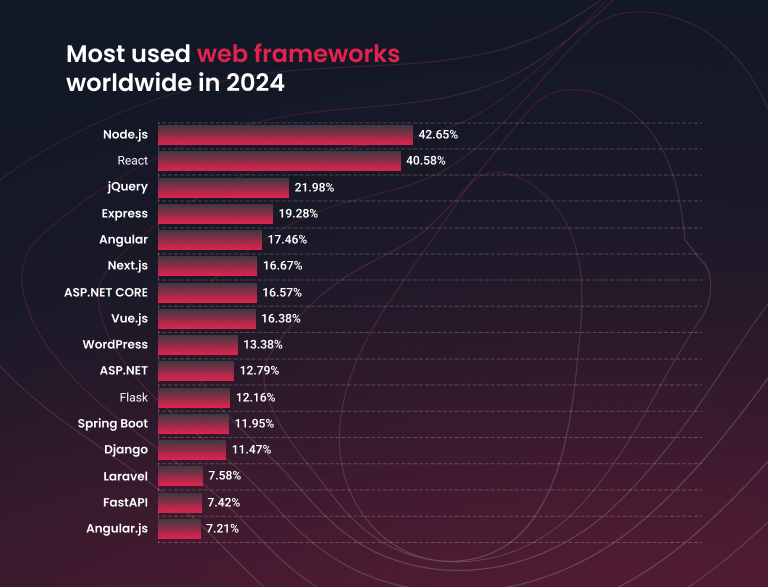
Node.js security vulnerabilities: how much could your business lose?
- The ItGovernance found a significant increase in the number of cyberattacks over the last few years, with 35,900,145,035 known records breached in 9,478 publicly disclosed incidents in 2024.
- According to the latest report by the Ponemon Institute, the average cost of a data breach in 2024 is estimated to be $4.5 million, a 12% increase from 2020.
- Comparitech analysed several NASDAQ-listed companies and revealed that those subjected to data breaches demonstrated a market underperformance exceeding 15% within three years. This is the result of a mix of factors, such as a bad reputation, increased churn rates, and other related effects.
- Atlassian estimates that for small businesses, a single minute of downtime can cost approximately $427. For medium—and large-sized enterprises, this figure escalates significantly, reaching up to $9,000 for every 60 seconds of lost operation.
Why should you build a secure Node.js app?
Building a secure Node.js application is important for at least three reasons.
Protecting user data
Your application likely handles sensitive user information like personal details, login credentials, payment data, and confidential business insights. If we don’t protect this data, we could face hefty fines from privacy regulators, possibly totaling millions of dollars. Implementing reliable security measures can protect user data and mitigate the risk of legal consequences.
Safeguarding application functionality
When there are security gaps, hackers can take advantage of them to mess with your services and data or even insert harmful code, which can seriously disrupt your backend. By putting good security measures in place, you can make sure your users have a smooth experience without any disruptions.
Preserving reputation
A security breach can really damage your reputation and cause people to lose trust in your service. Customers and users expect their data to be handled securely and your application to function reliably. A breach could lead to a loss of trust, while a strong focus on security proves your dedication to maintaining quality standards.

One might assume that following coding and architectural best practices is enough to address security issues. However, this is not the case.
Node.js’s advantages lie in its vast NPM ecosystem with millions of libraries. However, a significant portion of NPM packages contain security vulnerabilities. Simply put, the security of your Node.js project depends on the security of its dependencies.
Top 5 risks for security in Nodejs
Like any application, those built with Node.js come with their own set of security risks.
Cross-site scripting (XSS)
If a web application doesn’t thoroughly check user input, malicious actors could sneak in modified JavaScript code into the pages users visit. Browsers can’t tell if this code is trustworthy, so they just run it, opening up the possibility for attackers to access sensitive things like cookies, tokens, and user data.
Cross-site request forgery (CSRF)
A cross-site request forgery attack exploits user sessions by hiding malicious code within seemingly legitimate HTML elements. Since users are typically logged in and authenticated, clicking on these camouflaged links allows the attacker to make unauthorised changes within the underlying systems.
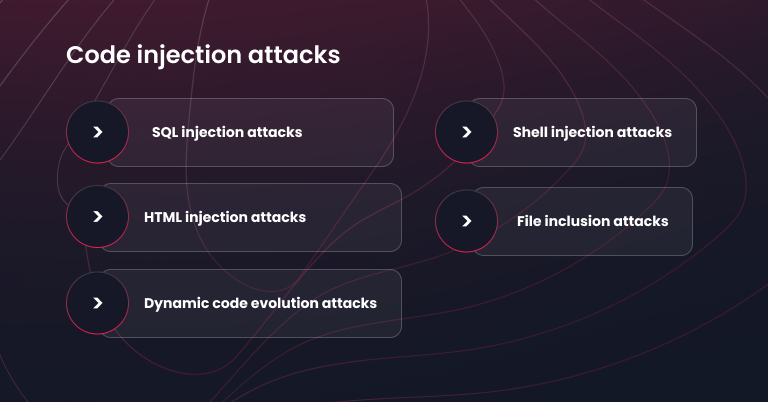
Harmful code injection attacks
By exploiting an input validation flaw, attackers can inject malicious code into your codebase, affecting the performance of your application. This application code injection technique grants them access to sensitive data, insights into your environment, or the ability to infect your system with malware.
Distributed denial of service (DDoS) attacks
In a DDoS attack, hackers overwhelm production servers with excessive internet traffic to disrupt regular operations. This traffic flood can overwhelm the system, causing considerable damage and outages. For example, Node.js versions 4 to 4.1.1 contained a flaw in HTTP, demonstrating how vulnerabilities can be used in such attacks.
Regular expression denial of service attacks (ReDos)
This kind of denial-of-service (DoS) attack functions by giving an input that makes a regular expression evaluation in the system take a long time, making the program slow and resource-intensive. This results in a slowdown of operations and the denial of service to legitimate users.
Find out how to choose the right Web3 tech stack for your project.
Node.js security best practices to eliminate brute force attacks
Now, let’s explore the Node.js security best practices.
Allow using secure passwords only
It is worth banning simple text passwords because they’re at risk of cyber attacks. Allowing users to create plain text passwords often leads to easily guessable combinations like “123456qwerty,” “asdfgh,” “strongpassword,” “AqSwDeFr,” and others, which are a welcome gift for seasoned attackers.
As you likely know, secure passwords should be at least 10 characters long and include a combination of uppercase and lowercase letters, numbers, and special symbols.
Secure your stored passwords with encryption
Storing “login:password” pairs directly in the database is risky. If an unauthorised user gains access to your database, they can quickly identify and extract this sensitive information, compromising all accounts regardless of password strength.
Encrypting passwords with reversible algorithms before saving them in the database adds a strong layer of security. But it’s really important to use equally trustworthy encryption methods to get the most security out of it.
Limit the number of login attempts per user per unit of time
Limiting the number of login attempts allowed within a specified timeframe limits the number of attacks. Hackers face a huge challenge because they have to sift through so many options within a short time, making it tough for them to break into the system.
Real end-users typically don’t need hundreds of login attempts per minute, so excessive login activity is a clear indicator of a potential attack. Limiting login attempts is super helpful for catching and stopping malicious actions.
Keep your Node.js and its packages up-to-date
The longer a software version is around, the more its weaknesses become known to the people who use it.
Consequently, outdated software frequently serves as an entry point for attacks. It’s really important to keep both the main Node.js framework and all its related packages up to date to meet security standards.
Always validate input data and output data
Many of the risks outlined earlier stem from inadequate validation of input and output data. Proper validation significantly mitigates security risks, including many forms of code injections, cross-site scripting, REDoS, and other attacks.
Validation should occur at both syntactic and semantic levels. Syntactic validation makes sure the syntax is correct, while semantic validation checks if the values entered into fields are accurate. Making sure you have strong validation procedures in place is really important for improving your application security.
Outsource your cybersecurity
The idea behind DDoS attacks is simple: flood your server with so many requests that it can’t keep up with processing them all.
Certain companies excel in preventing such attacks. For example, Cloudflare provides cloud DDoS security at a reasonable cost. Getting outside help for cybersecurity tasks, like DDoS protection, can be really helpful for dealing with different security issues effectively.
Monitor your cybersecurity regularly
Engage in frequent and systematic penetration testing to consistently monitor and evaluate the state of your cybersecurity infrastructure. Regular testing helps catch known vulnerabilities early on, possibly stopping problems from getting worse.
Additionally, ongoing assessments help identify any unauthorised changes within the system, thereby mitigating potential future risks.
Use Strict Mode
Strict Mode in JavaScript mitigates inherent legacy vulnerabilities. By restricting certain functionalities, it helps detect and rectify bugs that may go unnoticed in the standard mode. Additionally, activating Strict Mode has the potential to optimise application performance.
Enabling Strict Mode in Node.js entails adding the directive “use strict” at the beginning of the script. This action enhances security and promotes more reliable code practices within Node.js environments.
Don’t block the event loop
Certain requests processed through the event loop have the potential to block it, impeding the smooth management of subsequent requests and adversely impacting overall system performance.
In extreme scenarios of excessively high CPU load, such blocks can even halt the event loop altogether.
It’s important to manage callbacks carefully and ensure they run quickly to avoid blocking the event loop. One effective approach is to manage the length of callbacks, maintaining a consistent number of steps regardless of external factors.
This practice helps uphold the system’s responsiveness and reliability under varying workload conditions.
Send only what is necessary
It’s really important to tightly control the data you send outside of your system. This data could contain sensitive information from your customers or other parties, and hackers looking for weaknesses to exploit will target your data.
Carefully check all forms, emails, and APIs to make sure you’re only sending necessary information. By doing so, you minimise the risk of exposing sensitive data and strengthen your system against potential security breaches.
Use access control actively
Implementing an access control feature is the optimal solution for managing user permissions effectively. However, many Node.js tools lack built-in access control functionality.
Employing access control on each request facilitates the identification of potential routes for data breaches and expedites the resolution of any issues that arise.
A more polished method is to use middleware to enforce access rules, giving you complete control over user permissions across your application.
Final word
By putting security first, you protect sensitive data and maintain the trustworthiness of your customers’ information, especially in today’s constantly changing cybersecurity environment.
At Altamira, we help businesses seeking reliable and high-performing software solutions. Our seasoned team specialises in custom software development, delivering tailored projects to meet your unique requirements.
Whether you’re embarking on a new project or nearing completion, our developers possess the expertise to deliver exceptional results throughout the project lifecycle.
We deliver the following Node.js-powered web apps
- Real-time applications
- IoT solutions
- Collaboration tools
- Data streaming solutions
- Scalable apps
If you’re ready to kickstart your project or have questions, reach out to us today and discover the potential of our software solutions for your business.






