Effective cybersecurity has become even more crucial than business digitalization. According to the report from Juniper Research, the value of losses due to e-commerce fraud is expected to grow from $17.5 billion in 2020 to over $20 billion by 2021; a growth of 18% is projected over a single year. Strict tech security measures should be implemented with the support of a reliable IT partner.
Nowadays, data has become extremely affected by hacker attacks. It is not much wonder that business owners are increasingly strengthening cybersecurity. Depending on the nature of the hazard and the types of security vulnerabilities in e-commerce, building a reliable tech shield that prevents fraud and decreases losses to a minimum has become possible.
This article will discuss the critical e-commerce issues, security vulnerabilities, and the most effective strategies for creating a reliable security shield.
The key security threats to e-businesses
According to the Cisco definition, cybersecurity is an approach that includes several levels of protection. Security issues in e-commerce are paramount for entrepreneurs, aiming to introduce business improvements. E-commerce suffers greatly from cybercrime.
Due to the rapid development of technology in recent years, cybercrime became the number one business hazard affecting both customers and entrepreneurs. Cybercriminals often steal valuable private and financial data affecting millions of unsuspected customers.
They are skilled enough to hack the impressive number of databases which makes cybercrime a billion-dollar business on the black market. Among the most common reasons, making the databases vulnerable to cyberattacks is malicious software.
Due to the recent global digitalization, preventing cyberattacks and introducing reliable preventative measures using software has become the number one priority for e-commerce business owners.
Here are the common security vulnerabilities in e-commerce systems the businesses face today
- Cybercriminals steal credit card private details, personal identity credentials, and vulnerable organizational and government institutions’ data, hacking the digital databases. Only the latest software tools can fight the technological invasion of privacy.
- Threats do often come from external hazards. However, it’s also possible that the company’s “insiders” may cause common security vulnerabilities in e-commerce systems and invade sensitive internal data. Apart from the potential financial losses, loss of customer loyalty, and bad publicity, data breaches can have a tangible business effect.
- Fraudulent actions aimed at getting access to customer records and other sensitive information through network intrusions and attacks.
- There are other types of security vulnerabilities in e-commerce, aimed at extracting the business finances. These include expelled ransomware attacks when hackers encrypt the data and demand considerable financial reward to decrypt it.
The rapid spread of cybersecurity disruptions and common security vulnerabilities in e-commerce systems raised the necessity to elaborate on the efficient tech tools to deter, detect and block the inner and outer cyber threats, preventing the serious negative consequences for private e-commerce businesses.
Cybersecurity software is aimed at protecting digital networks, systems, apps, and databases from hackers, cyberattacks, and intrusions. Malfunctioned cybersecurity protections may cause serious business issues.
Avoid cyber attacks and challenges in e-commerce security with the help of our software solutions
Technological invasion of privacy can only be fought by the latest software tools. However, the choice of tools for solving privacy and security issues in e-commerce depends on the very nature of the cyber threat the business faces.
Investing in effective and reliable technology has proved to be a worthy decision that pays off in the long run. Let us take a deeper insight into common security vulnerabilities in e-commerce systems and discuss efficient software tools to overcome them.
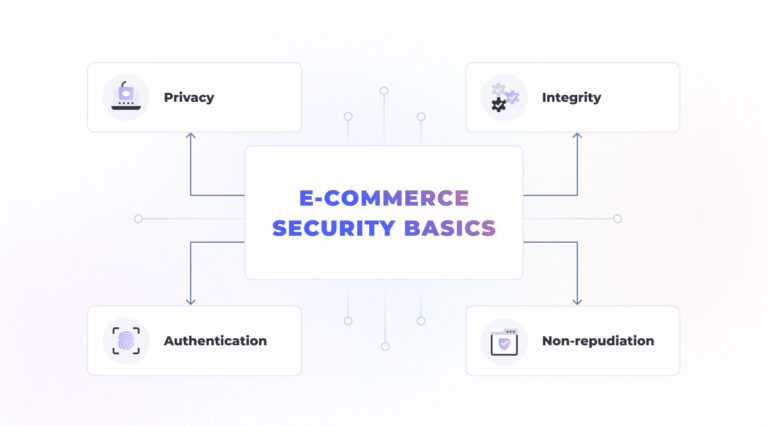
The ability to address the security aspects in e-commerce directly is driven by the deep understanding of threat nature and behavior.
Here is the list of the most widespread cyberattacks in e-commerce
Malware
The hazardous software that was built with social engineering tactics aimed at invading internet users’ systems and devices.
DDoS
Cyberattacks that are aimed at particular websites, systems, and servers. These attacks flood the victim with a variety of messages and connection requests. Mainly, they aim to disrupt business operations.
Phishing
Users are mainly attacked by e-mail by a credible and reputable person. These cyber thieves disclose personal information, targeting specific companies and individuals.
SQL injection
Criminals use SQL queries, aiming to access the databases. The query is designed to delete, change or create a database, or extract data from a given database.
XSS (cross-site scripting)
Injects malicious scripts and code into apps and the website content. It is aimed at getting session cookies, spreading malware, defacing websites, and phishing for private details.
Botnets
A connection of devices invaded and controlled by the cyberattacker. The most widespread cases include spamming, click fraud campaigns, and generating traffic for DDoS attacks.
Credit card fraud
The cyber thief receives unauthorized access to the customer’s credit card and personal information.
With the constantly evolving challenges in e-commerce security, disruptions, and attack methods, new security needs arise.
Since data volumes and the number of digital operations grow as well as the use of cloud and the IoT, the opportunities for attacks expand. It creates the necessity for building reliable software and raises cybersecurity awareness among business users.
Cybersecurity software assists in overcoming challenges in e-commerce security by
- Building a zero-trust framework that demands authentication of users and devices;
- Introduction of a few layers of authentication for user validation, commonly including two-factor authentication approaches;
- Sensitive data privacy and protection through tokenization;
- Creation of handy tools for high-level management and protection, data loss prevention, and customer behavior monitoring.
Security aspect as a guarantee of reliable software development
According to the latest technology trends, the aspect of security should be integrated from the preliminary stages of development. Security assessment and development stages are being simultaneous processes through the whole delivery cycle.
The most successful security strategy lies in the automation of basic security procedures with control and assessment at preliminary stages, not only when the product reaches the QA team.
Altamira experts implement automation of the security testing at the beginning of the product development, and it allows to reduce the administrative disruptions thus minimizing the possibility of errors leading to downtime or cyberattacks.
Bringing development and security teams working together allowed increasing enhance the security due to shared responsibility, in-time bug detection, and elimination.
Thus, you will not have to redesign the whole product or make additional investments to introduce new features and changes after the deployment.
How to build security into the products at preliminary stages
- Continuous monitoring – it allows tracing and blocking suspicious issues before they cause serious disruptions.
- Threat modeling for each project. It means you identify the threats and vulnerabilities thus discussing the measures to overcome them. It raises security awareness and allows efficient risk identification.
- The right allocation of time and resources. Risk assessment and threat modeling allows us to identify the vulnerable areas to focus on.
- Initiate the security on boot-up. Software vendors should implement a series of boot testing to make sure that the software is authentic.
- Security should be an equal player in the whole development process. Security should be an integral part of the company’s development culture. Every participant in the project is responsible for security.
- Screen your vendors, contractors, and employees before signing the contract.
- Aggressive code testing. Focus on the attack that addresses vulnerabilities to develop a resilient code.
Evidence of vendor's security and proven quality
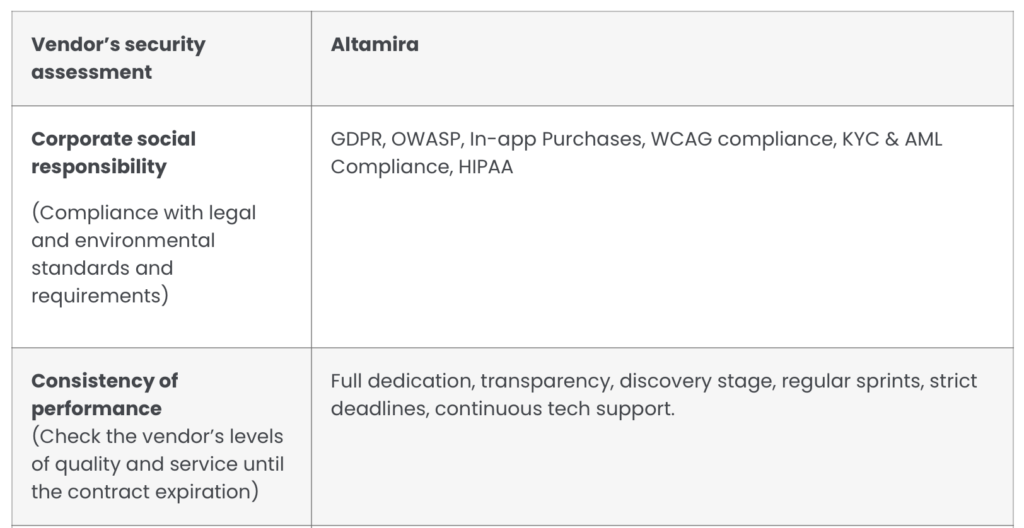
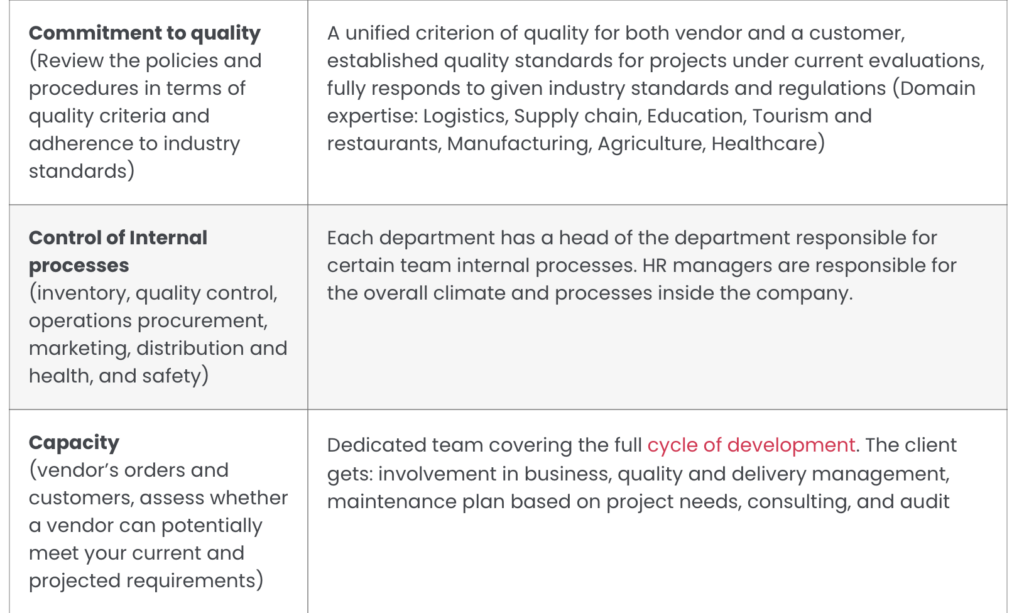
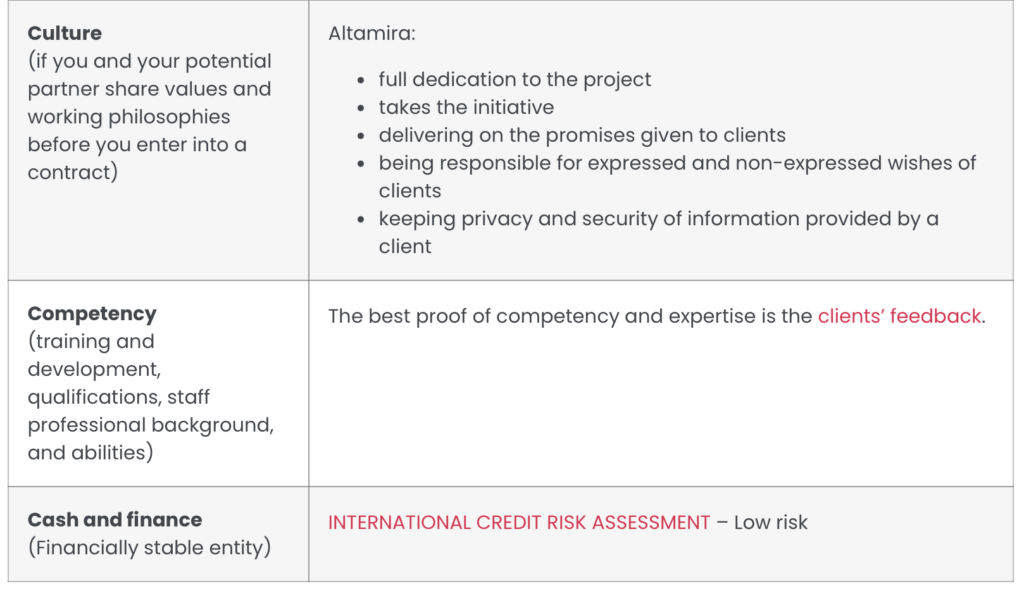
Altamira powers up your cybersecurity with the best software
Lack of security measures usually leads to financial losses, reputation damage, valuable data leaks, making your business vulnerable in the global arena and affecting business continuity.
The basics of cybersecurity involve the security of sensitive data that is impossible without a reliable technology partner. To manage the data, you need IT systems that can reduce risk, keep your system secure, and protect private information.
How Altamira can secure your e-business
- AI- and ML-powered tools;
- Strong system backup planning and cloud backup options;
- Data security enhancements through efficient data encryption, identity, and access management tools, building PKI infrastructure;
- Endpoint security with antivirus solutions that are continuously updated;
- Solutions for data loss prevention, securing the control of valuable info and environment;
- Building enterprise-level intrusion detection and prevention systems to cope with malicious activities throughout your environment;
- Solutions for enterprise wireless security;
- Ensure that all communication between edge devices is encrypted;
- External security assessment through extensive in-depth testing;
- Acceptable use practices;
- Cloud protection instruments.
Altamira is a reliable IT partner that keeps your e-business strong and stable. We are ready to deploy endpoint security solutions and build robust threat response tools to manage the security issues.
We have 10+ years of experience in the market, building solid software solutions for many industries, including e-commerce as well.
Our experts build the software solutions that help to
- Automate and scale web scanning tools to protect your organization, reputation, and private data of your customers;
- Regularly discover new vulnerabilities ahead of cyber attackers;
- Secure your sensitive data;
- Efficiently address all types of cyber threats;
- Our experts conduct security testing through efficient security assessment and vulnerability management.
Our experts understand your budget and can adapt current architecture to find the best ways to expand your business security measures with industry-tailored solutions.
The Discovery stage enables you to uncover the weak points of your business and turn them into advantages, building the exact project objectives and putting the idea of a customer into reality.
Altamira also has rich experience providing dedicated teams that are fully focused on the implementation aspects while the client controls the entire workflow.
The cost of cyberattacks
Fact that a cyberattack can hazardously influence all the aspects of your business and put a negative stamp on your brand name, IBM has counted the real cost of privacy and security issues in e-commerce.
According to their report, businesses have to spend on average 280 days to detect, analyze and eliminate the threats after a breach. That reaches $3.86 million worldwide while in the USA the number is up to $8.64 million per breach and continues to grow even further.
In the business world, your primary concern should be your reputation, the security of your clients, and their sensitive data.
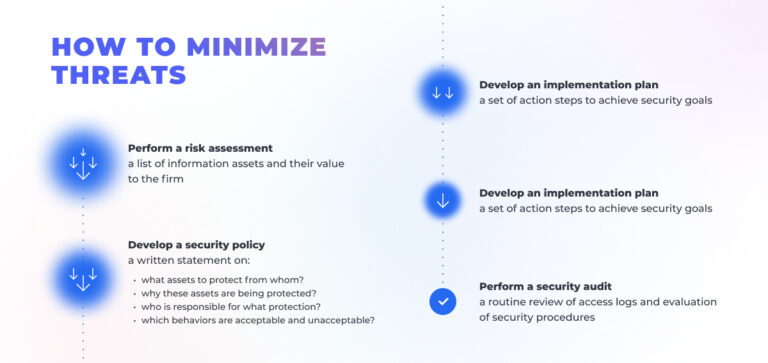
Here are the efficient steps to create a reliable security backbone for your brand name
- Schedule the risk assessment procedure with the software experts who will examine all systems and analyze dependencies, uncovering inefficiencies and vulnerable points.
- Use the outcomes to evaluate the risk probabilities and their current hazard.
- Put efficient measures in place by implementing individual business strategies for successful risk mitigation and enhancing the overall level of cybersecurity.
- Gaining control over the security risks and becoming aware of the potential hazards by creating a cybersecurity strategy.
- Taking preventative measures knowing how cybercriminals achieve their objectives puts you one step ahead of the game.
Customer concerns regarding e-commerce and strategies to eliminate them
Investing in tools to solve the security issues in e-commerce pays off in the long run. It has proven to be more than just a defensive measure, providing considerable advantage and enhancing compatibility. Privacy violation is among the top reasons why users do not trust their private credit information to retailers.
With the current situation the pandemic has created, more and more people prefer online services rather than offline options, and cybersecurity directly influences their choice of online options.
In 2012, senior staff writer for Wired Magazine Mat Honan had his Amazon, Twitter, Gmail, and Apple accounts hijacked.
Cybercriminals managed to exploit Apple and Amazon’s over-the-phone identification procedures to break into the accounts. Thus, even the leaders become vulnerable when overlooking the main types of security vulnerabilities in e-commerce.
Most of the customers are not ready to provide credit card numbers and personal data to e-services since they still have serious concerns about the security issues in e-commerce while ordering online.
Since almost all customers interact with e-commerce services via phone or email, such websites are particularly vulnerable to social engineering attacks.
However, the lack of consumer confidence can be efficiently compensated with the strategies, allowing to provide s safer e-shopping experience. Here is the list of the most efficient steps to enhance security aspects in e-commerce:
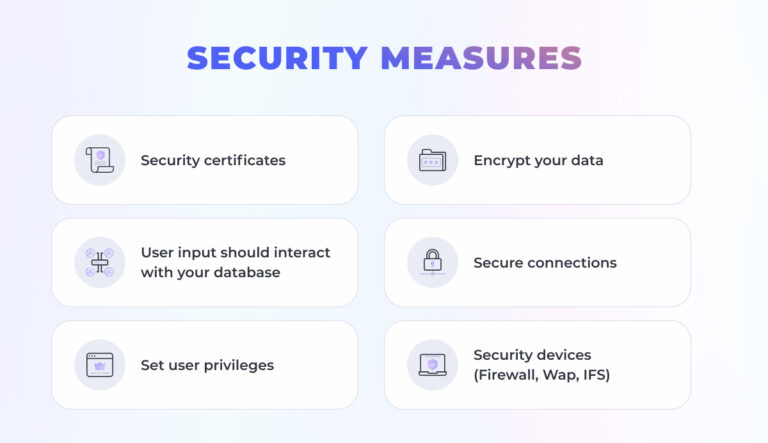
- Choice of a reliable web hosting provider. The level of security depends on the tools the hosting provider utilizes. Make sure they provide reliable backup and recovery, scanning and protection against the malware, standard time, and protection against DDoS attacks.
- Encryption of sensitive data and strict confidentiality measures. Reliable e-commerce suppliers should encrypt such details as tokens, billing details, emails, etc.
- Utilization of secure software.
- Security certificates.A unique digital ID number is used to verify the identity of an individual website or a user.
- Wise authentication. The service implements the mechanism to authenticate a user before giving access to any specific information. Moreover, SMS authentication, authentication via phone call, and email confirmation are reliable and efficient authentication methods.
- Secure online transactions. Personal data should not be altered during the transmission over the network and the time of the session must be limited.
- The use of HTTPS. You should see a notification in your browser when a secure connection is used. Moreover, it allows getting a higher Google rank.
- Automated website backups. Backups allow eliminating problems with broken pages and website hacks.
Experts at Altamira always make sure that the information on the server and code integrity are under protection
We conduct regular file reviews, keep track of abnormal activity, and provide daily statistics on logs. We also use HTTPS by default to ensure that the data (personal, credit card, etc.) is transferred in the encrypted form.
As we mentioned earlier, you can get in touch with us to discuss your current security situation and change it for the better. We offer a free consultation with our expert, who will help you with the selection of the right security approach for your company.
So don’t wait until something happens, protect your business beforehand with the Altamira team and be sure that all your data and systems are safe.
Final thoughts
E-commerce stores customer data like credit card details, bank account info, and private data details. With no special attention to security aspects in e-commerce, the entrepreneur will not gain customer loyalty for sure.
The enforcement of security measures should be the number one priority for e-commerce to avoid hazardous financial consequences and gain the trust of your customers.
There’s no silver bullet approach to cybersecurity, however, the complex approach on all layers of security enables the desirable results.
The in-time identification of common security vulnerabilities in e-commerce systems and implementation of reliable and efficient software against security issues will increase your level of cybersecurity. E-commerce should concentrate on cybersecurity as a holistic solution to protect customers.
FAQ
Cybersecurity in e-commerce is a holistic term that implies the protection of customers, internal operations and technology as well as consumer information.
With the constantly evolving disruptions and attack methods, the new security needs arise. Since data volumes and number of digital operations grow as well as the use of cloud and IoT, the opportunities for attacks expand.
It creates the necessity for building the reliable software and rise cybersecurity awareness among business users.
E-commerce suffers greatly from cybercrime. During the recent years, due to the rapid development of technology, cybercrime became the number one business hazard affecting both customers and entrepreneurs.
As it is often the case, cyber criminals steal valuable private and financial data affecting millions of unsuspected customers.






