Artificial intelligence (AI) has tremendous potential in cybersecurity, a rapidly growing field. Businesses are worried about growing cyber threats, and rightly so: just one successful malware attack can cause a lot of financial, reputational, and legal damage, even stopping a business. But thanks to advanced AI-powered cloud security, the future looks much more promising for businesses than for cybercriminals.
Cybercriminals don’t need to be technical experts today. Artificial intelligence allows them to use specific automated tools that can be trained in the process. It has already become common for malware to set a time interval, after which it will manifest its malicious activity – it can be minutes or even days after the file has been declared safe.
Some businesses with limited security resources are likely to be the most vulnerable. Everyone is at risk as AI-based ransomware and other forms of malware are incredibly efficient at spreading and hitting targets with precision. The AI war, which is industrial and political espionage and intelligence gathering, is another growing threat. Even the German parliament has suffered from such cyber operations.
The biggest lesson to be learned from this is that many traditional security measures are no longer good enough. Artificial intelligence works just like the human brain: it learns, develops, and grows. No firewall or built-in virus-checking program can compete with this.
According to the FBI’s 2020 Internet Crime Report, the number of cybercrimes increased by 61% compared to the previous year. The total damage was $ 4.2 billion.
AI, Machine Learning, and Deep Learning in cybersecurity
In the foreseeable future, machine learning AI will become an essential cybersecurity tool. And although, at present, cybersecurity still largely depends on the work of specialists, machines are gradually taking the lead in solving specific problems.

Technological optimisation makes the human role in the field of security more effective. These developments relate to the following main areas:
Artificial intelligence (AI) is designed to fully endow the machine with the ability of the human mind to respond. It is a core discipline that encompasses many others, including machine learning and deep learning.
Machine learning is a process in which a computer, using specialised technological tools, can study and use new data without mandatory human intervention. Sophisticated algorithms allow a digital platform to process and “understand” data from vast repositories of information to reach certain conclusions and discover patterns.
The system analyses these patterns, groups them according to certain criteria, and then makes conclusions or assumptions. In traditional machine learning, a computer learns to decode information that people have already categorised and labelled. Machine learning is the most relevant discipline in AI-powered cybersecurity today.Deep learning is another level of our pyramid since it is a subset of machine learning. The main difference between them is that deep learning uses neural networks, a complex structure of algorithms, the creation of which was inspired by a human brain. It’s a more advanced technology that doesn’t require specific instructions from programmers to learn from data. Currently, deep learning in cybersecurity belongs to the realm of machine learning, so we will mainly focus on this broader area.
The role of Machine Learning in cybersecurity
Security software using machine learning technologies is different from the traditional concept of artificial intelligence. This approach uses data templates to determine the likelihood of an event.
It means that the algorithm operates by learning from a dataset focused on a specific task. Its job is to find the best way to accomplish a given task. ML will strive to find a solution that is the only one possible based on the available data.

Machine learning technologies are great at tackling repetitive tasks, such as identifying patterns in data and validating them. But humans have to interpret the data, while machine learning helps bring the data into a readable and analytic form.
The more this program repeats the cycle of recognising and assigning categories to patterns to conclude them, the better it “understands” how it can be done on its own, without human help or additional scripts written by people.
You can come across many different machine learning algorithms, but they all usually perform one of the following tasks in cybersecurity:
Regression
Finds correlations between different datasets and understands how they relate to each other. You can use regression to predict operating system calls and then identify anomalies by comparing the forecast with the actual request.
Clustering
Analyse datasets and group them based on the general characteristics of this data. Clustering works directly with new data without considering the previous examples.
Classification
In this approach, algorithms are trained from previous observations and try to apply the knowledge gained to new data. Classification involves identifying artefacts and assigning them one of several labels. For example, a binary file could be classified as legitimate software, adware, or ransomware.
Recommendations for further action
These guidelines will help you improve the effectiveness of your machine-learning security controls. They are inferred based on behavior patterns and previous decisions. In other words, it is an adaptive system capable of building logical relationships based on available data. Such tools can help with threat response and risk management.

The synthesis of possibilities allows you to get completely new results based on historical and new datasets. This approach allows for a better determination of the probabilities of repeating past states of the system. For example, synthesis can be used to investigate vulnerabilities in an organisation’s systems proactively.
Forecasting is the most advanced of the machine learning processes. Potential outcomes are determined by evaluating existing datasets. Forecasting can be used primarily for threat modelling, fraud prevention, and data loss protection.
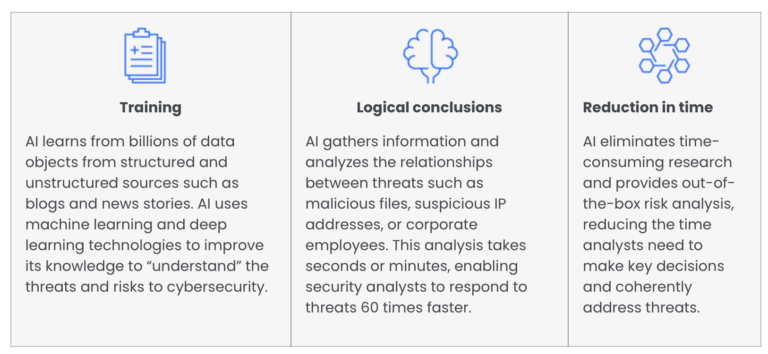
Benefits of Artificial Intelligence in cybersecurity
AI technologies such as machine learning and natural language processing enable analysts to respond faster and more confidently to threats.
It is important to note that AI can perform essential functions: centralised processing, power redundancy, internal temperature, and cooling filters. This way, you can optimise costs with AI. AI can help keep track of hardware failures. AI alerts let you quickly troubleshoot hardware problems.
AI's role in enhancing threat detection in cybersecurity
Artificial intelligence is transforming cybersecurity by significantly improving threat detection. AI-powered algorithms can analyse massive datasets from various sources, recognising patterns and identifying unusual activities that may indicate potential cyber threats.
Unlike traditional security systems, AI can process both structured and unstructured data, making it highly effective in spotting anomalies and predicting cyberattacks before they occur. By continuously learning from new threats, AI enhances security posture, allowing organisations to stay ahead of evolving risks.
Enhancing cyber threat intelligence with AI
AI plays a crucial role in cyber threat intelligence by collecting, integrating, and analysing security data from multiple control points. This capability improves situational awareness and enables proactive threat hunting.
AI enhances the accuracy of risk assessments by providing real-time insights, making it easier for security teams to address vulnerabilities before they are exploited. With AI-driven behavioral analytics, organisations can analyse vast amounts of user and device data to detect insider threats and unauthorised activities.
Predictive analytics for cyberattack prevention
One of AI’s most valuable contributions to cybersecurity is its ability to predict and prevent cyberattacks. By analysing historical data and recognising trends, AI can identify malicious activities before they escalate.
AI-powered systems can differentiate between normal and suspicious behavior, improving threat detection accuracy while reducing false positives. Additionally, AI-driven predictive analytics enhances breach risk prediction, ensuring organisations can implement preventive measures before an attack occurs.
AI-powered insider threat detection
Insider threats pose a significant challenge to cybersecurity, as they often bypass traditional security measures. AI enhances insider threat detection by analysing user activity, identifying unusual behaviors, and flagging potential risks.
By continuously monitoring user behavior and access patterns, AI helps organisations prevent accidental data leaks and malicious insider actions. Furthermore, AI systems adapt to changing environments, improving their ability to detect subtle deviations that may indicate security threats.
AI-driven behavioral analytics in threat hunting
AI enhances threat-hunting processes through advanced behavioral analytics. By analysing vast amounts of security data, AI can uncover hidden patterns, detect suspicious activity, and provide security teams with actionable insights.
AI-driven behavioral analytics improves the efficiency of cybersecurity teams by automating data analysis and reducing response times. This technology enables organisations to strengthen their security strategies and better protect their digital assets from sophisticated attacks.
Automating incident response with AI
Incident response is a critical aspect of cybersecurity, and AI significantly streamlines this process. AI-driven security systems can automate responses to various threats, minimising the time required to mitigate risks.
By analysing security events in real-time, AI reduces human intervention in repetitive security tasks, allowing analysts to focus on high-priority threats. Additionally, AI-powered Security Orchestration, Automation, and Response (SOAR) platforms integrate incident detection, analysis, and response, improving overall security efficiency.
Automated vulnerability scanning and patching prioritisation
AI enhances vulnerability management by automating scanning processes and prioritising patches based on risk levels. AI systems analyse software code, network configurations, and historical attack patterns to identify security weaknesses.
By reducing the time required for manual assessments, AI improves the efficiency of vulnerability remediation. Automated patch management ensures that critical vulnerabilities are addressed promptly, reducing the likelihood of exploitation by cybercriminals.
Enhancing situational awareness with AI
AI enhances situational awareness by analysing security data in real time. This capability allows security teams to respond quickly to potential threats, improving risk management strategies. AI-driven security solutions offer a more comprehensive view of an organisation’s security landscape, enabling proactive defense measures.
By continuously monitoring and adapting to new threats, AI enhances the resilience of cybersecurity frameworks.
Risk management through AI-driven technical insights
AI contributes to risk management by providing detailed technical insights into security environments. AI-driven analysis helps organisations identify vulnerabilities, optimise resource allocation, and implement effective risk mitigation strategies.
By analysing network traffic, system logs, and user behavior, AI enhances decision-making processes, allowing security teams to focus on the most critical threats. This approach improves overall security efficiency and reduces the likelihood of security breaches.
Cost reduction through improved threat detection accuracy
AI improves threat detection accuracy, reducing operational costs associated with cybersecurity incidents. By automating security operations and minimising false positives, AI reduces the burden on security analysts and enhances response times.
AI-powered solutions optimise resource allocation, ensuring that organisations can maintain strong cybersecurity defences without excessive expenditure. The ability to detect and mitigate threats more efficiently translates into long-term cost savings and improved security resilience.
By continuously monitoring and adapting to new threats, AI enhances the resilience of cybersecurity frameworks.
Use cases of AI / Machine Learning in cybersecurity
Machine learning allows you to view volumes of data and analyse them using statistics quickly. In modern business, a considerable amount of information appears every day, so technology’s introduction helps to cope with this.
AI-based user behavior modeling
Some types of cybersecurity attacks that target corporate systems are carried out by stealing data from specific users in an organisation. Malicious users, disguised as users, penetrate the system and gain access to the corporate network in technically legal ways, which means that their trail is challenging to detect and stop.
AI-based cybersecurity systems can recognise the behavior patterns of specific users to detect changes in their behavior patterns. In other words, technology notifies the security team when this happens.
Darktrace has implemented a cybersecurity solution that uses machine learning to analyse network traffic’s raw data to understand the baseline level of the normal behavior of every user and device in an organisation.
The software learns by using training datasets and raw data from experts to distinguish between significant deviations and normal behaviour and immediately alert the organisation to cyber threats.
The best thing about implementing AI concepts is that companies can reduce their cost by 12% in terms of threats and breach detection. In addition to this, they can follow use cases of AI to improve their performance cybersecurity-wise.
AI for fighting AI threats
Today, increasing the detection of cyber threats is crucial for company security. Hackers now use AI to find weak points through which they can penetrate corporate networks. Thus, deploying AI software to defend against AI hacking attempts can become a necessary part of tamper-proof protocols.
Over the past several years, companies around the world have come under cyber and ransomware attacks. Imagine that in the first half of 2020, companies incurred losses of $ 3.86 billion.

Falcon Platform is a digital security solution that uses AI to defend against ransomware threats like WannaCry and others. The software is reported to identify anomalies to ensure endpoint security on corporate networks.
AI for identifying online threats
Protecting corporate networks is critical to your business. It is essential to understand all the elements involved in the network topography to provide genuinely high network security. For cybersecurity professionals, this means keeping track of all communications in and out of the enterprise network.
Managing the security of these corporate networks includes determining which connection requests are legitimate and attempting to exploit unusual connection behaviour.
The challenge for cybersecurity experts is to determine which parts of an application, be it the web, mobile platforms, or applications in development or testing, might be malicious.
eSentire offers an AI-powered enterprise cybersecurity software called the VSE Versive Security Engine. They claim they can help banks and financial institutions analyse large datasets of transactional and cybersecurity-related data using machine learning.
Versive uses banks NetFlow (a network protocol developed by Cisco for collecting IP traffic information and monitoring network traffic), proxy server, and DNS data (computer network data) as input to the Versive Security Engine.
The digital solution can also monitor corporate networks using anomaly detection, which is similar to the events in past cyber threats.
IDC expects worldwide security spending to reach $174.7 billion in 2024, with a compound annual growth rate (CAGR) of 8.1% over the 2020-2024 forecast period.
Final words
The use of artificial intelligence in cybersecurity is more of an innovation than something generally accepted. Some companies are improving their systems with cybersecurity specialists, who, in turn, are working on software to identify cyberattacks more accurately.
It is essential to understand that you will receive a system that is as good as the quality information you provide for training it.
Some multinational companies already have a team of specialists in cybersecurity, IT infrastructure, and budgets to develop products for working with massive data.
FAQ
Saxe J., Sanders H. Malware Data Science. Attack Detection and Attribution, 2018. The book contains detailed solutions to real problems in the field of detecting and automating the analysis of malicious programs.
Chio C., Freeman D. Machine Learning and Security, 2018. The book contains a large number of examples of Python code.
Tsukerman E. Machine Learning for Cybersecurity Cookbook, 2019.
Chebbi C. Mastering Machine Learning for Penetration Testing, 2018. The disadvantage of the book is that it does not provide a deep analysis of the problems to be solved and an argument for the methods used. The author answers the practical question, “How to solve the problem?”. But it does not answer the question, “Why in this way?”
Machine learning uses existing behaviours to make decisions based on available data and inferences. Thus, it does an excellent job with monotonous tasks, such as tasks in which a person may experience a blurred eye effect.
One of the main advantages of ML is its speed of detecting and responding to a cyber-attack. However, human intervention is still required to make the necessary corrections since the pedestrians are trained, and it is essential to monitor that the algorithm works correctly.
Increasing the scale of resistance Artificial intelligence can also increase the system’s resistance to constant attacks. If a corporation uses multiple hardware devices, such as desktop computers and mobile phones, to communicate and transfer information, the chances of a cyber attack to extract data from the system are high.
Ability to confront every incoming threat. When responding to an attack, AI-powered machine-driven mechanisms can counter each incoming threat as it presents itself and take countermeasures in real time. Artificial intelligence has had some cybersecurity impacts.
Developing an effective strategy against threats In typical security configurations, real-time response to threats is often constrained by the speed and sometimes the changing nature of the attack itself. Therefore, analysing a large amount of data is necessary to formulate an answer and outline the right strategy.
AI strengthens cybersecurity by automating and improving threat detection. It can scan vast amounts of security data—such as network logs, user behavior, and system activity—to identify unusual patterns that may indicate an attack. AI also enhances email security by detecting phishing attempts, filtering out malicious messages, and preventing users from falling for scams. Additionally, AI-powered security tools monitor endpoints to detect and block suspicious activity in real time.
AI analyses large datasets from various sources, spotting threats that traditional methods might miss. By recognising behavioral anomalies—such as unauthorised access attempts or sudden changes in system activity—AI helps detect insider threats and potential breaches. It can also automate vulnerability scanning, prioritise security risks, and even take preventive action, reducing the workload for security teams while improving accuracy.
AI leverages machine learning to analyse past attack patterns and predict future threats. By continuously monitoring network traffic and user behavior, AI can identify early warning signs of an impending attack—such as unusual login attempts, suspicious file transfers, or irregular data access. This predictive capability allows organisations to take proactive measures, strengthening their defenses before an attack occurs.
AI leverages machine learning to detect cyber threats by continuously analysing vast amounts of security data. Machine learning models are trained on historical attack patterns, allowing them to recognise both known threats and emerging risks.
Supervised Learning: AI is trained on labeled datasets containing examples of cyber threats. Based on past incidents, it can accurately identify malware, phishing attempts, and unauthorised access attempts.
Unsupervised Learning: AI detects anomalies by identifying deviations from normal network behavior. This helps uncover unknown threats, including insider attacks and novel hacking techniques.
Deep Learning: AI-powered deep learning models can precisely distinguish between legitimate and malicious behavior by analysing network traffic, user activity, and system logs.
By continuously refining its models with new data, AI improves its ability to detect threats with minimal false positives, helping security teams respond more efficiently.






