Mobile devices have become more popular than laptops. No wonder – they are always in our hands and allow us to engage in so many activities on the go. We have mobile applications for everything – online shopping, entertainment, communication with friends, bank operation, and even work. According to recent research, people in the US spend around 88% of their time using mobile applications. Impressive, isn’t it?
Speaking about businesses – they tend to go mobile as well actively. A growing number of companies seriously consider custom mobile application development. And while all startuppers and business owners keep being concerned about the feature set and design of their future mobile applications, we insist on taking good care of mobile security.
In today’s post, we would like to discuss the security of custom mobile applications, unveil common security loopholes, cover the best security practices and share our own valuable experience. All this information will help you develop a reliable mobile application that will be completely hacker-proof and, therefore, last you for years. So let’s wait no further and delve into this topic right away!
Influence of weak mobile app security on business
To begin with, let’s speak about the role of mobile app security and what can happen if you neglect it. Verizon report from 2020 revealed that 43% of companies had sacrificed the security while deploying their mobile applications, and 39% of companies admit that they faced a security breach that impacted their business.
In general, 97% of different businesses faced mobile threats last year. Why did it happen? Simply because some companies did not devote any budget to mobile security, did not scan the code of their apps for vulnerabilities, and even skipped crucial testing steps.
It is hard to imagine how much money the companies spent on fixing all security-related issues and dealing with their consequences. But apart from the financial loss, they faced other, way more serious issues that we will cover in this post.
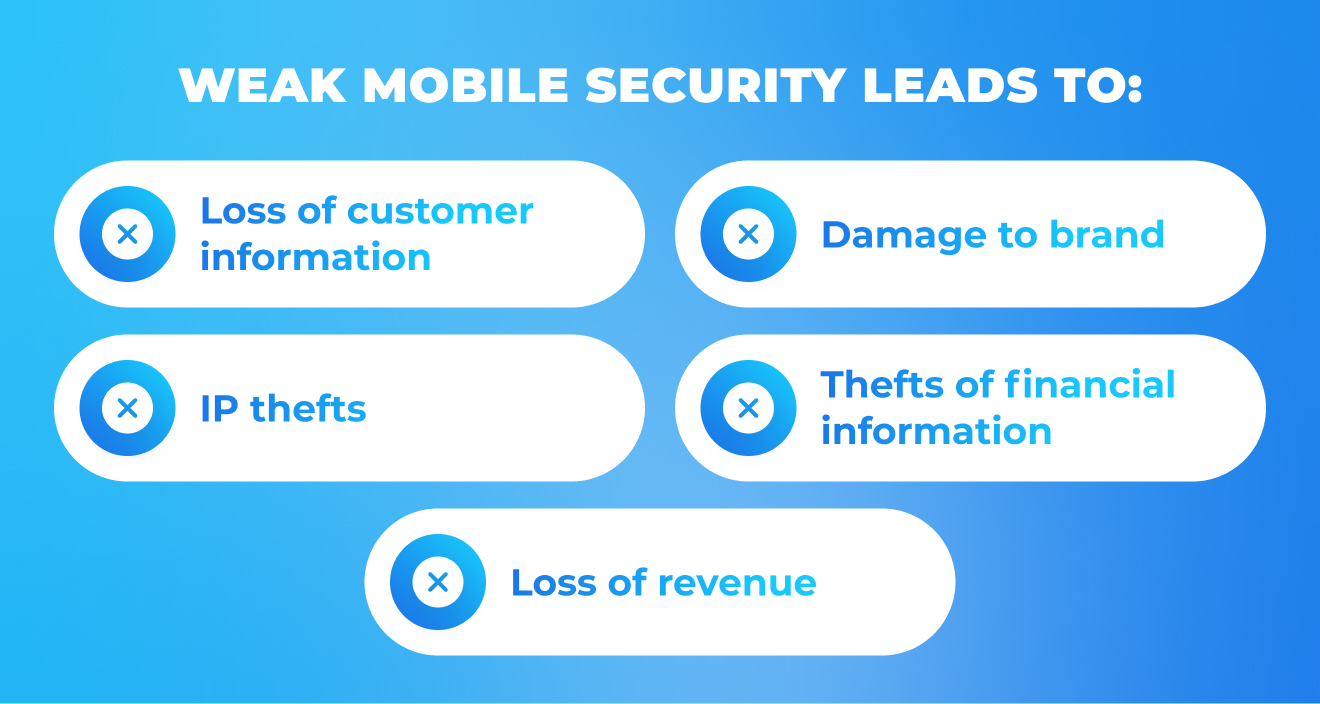
Common security risks in iOS and Android apps
Now when you know what impact weak mobile security can have on your business, it is time to discover what common security risks you may face. For more than ten years in business, Altamira developed lots of iOS and Android applications. And of course, we explored all possible risks, experienced development challenges, and found ways to protect mobile solutions properly.
Now we’d like to share all our accumulated knowledge with you so you can get an upper hand while fighting mobile frauds. To begin with, please take a look at the infographics demonstrating 10 main mobile security risks provided by OWASP:
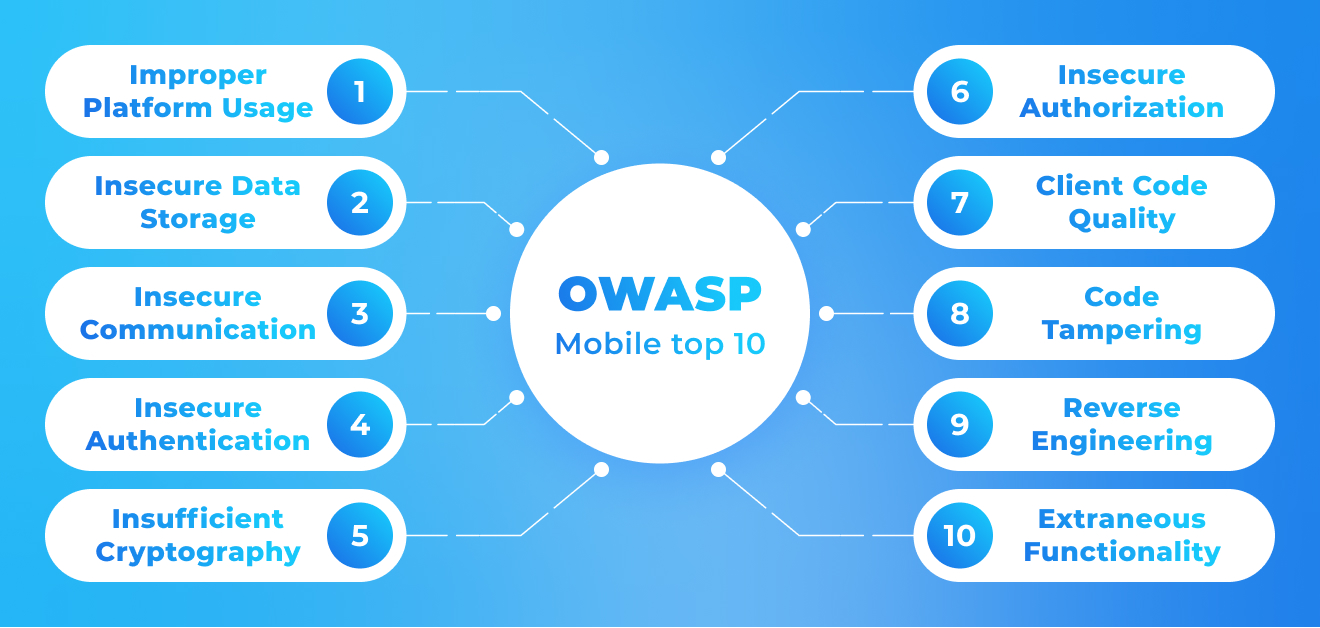
As you can see, the list is pretty solid and developers need to minimize all these risks using their coding skills and rely on advanced testing tools. Apart from the OWASP list, there are way more common risks that users of mobile apps can face. Here are the top five of them:
Possible iOS security risks
Everyone knows that Apple is focused not only on innovation but also on the security of every device and solution they release. And they demand the same attitude and dedication from the iOS developers. It is not a secret that submitting an app to the App Store can be stressful and take a long time. The apps are thoroughly checked by the responsible Apple team and only if everything meets the standards, the app is approved.
However, despite high standards and strict demands, some vulnerabilities are still left in iOS devices that can help hackers steal passwords, banking information, and personal data. So to secure your iOS application, you need to address the following risks:
- Usage of insecure databases – lots of iOS apps store their data in SQL databases, binary data stores and cookies, which are easy targets to hackers. Therefore it is crucial to choose the right database for your solution to avoid data leaks or exposure.
- User authentication – there is a device-level security in iOS, which includes Face ID and Touch ID. And while some developers consider that these systems are enough to protect data or services in the iOS apps, in fact, that data is very exposed. iOS apps require serious user authentication, and it’s the responsibility of developers to implement it.
- iOS jailbreaking – this operation implies finding a weak point in the kernel and then running unsigned code on a mobile device. This means that a person can access the file system of an iOS device. Jailbreak can seriously harm the device, decrease its performance, compromise safety and cause update difficulties.
Well-known security issues in Android
Android devices have less strict standards than iOS ones. However, developers, in any case, need to make sure that their apps don’t have major security loopholes that can cause major damage. The list of the most common security issues in Android apps includes but not limited to:
- Rooting – Android users know that they can easily root their devices using third-party applications, but what they don’t know is that rooted devices are easy targets for hackers. So for the developers, it is important to make sure that their Android apps do not work in a rooted mode or work with interruptions and issue warnings to users.
- Irregular updates – every now and then Android team finds some OS vulnerabilities and releases updates to fix them. Therefore the developers should monitor those OS updates and never neglect security patches.
- App permissions – these days apps ask users for so many permissions when you first download and launch them. The permissions users grant to an app can bring potential security risks. Therefore secure apps should ask for as few permissions as possible to avoid stealing and misuse of users’ data.
How to make your custom mobile app secure
What can be more difficult than developing a feature-rich mobile application? Well, its probably developing a feature-rich application that is risks-free. Before a custom mobile solution ends up in the mobile store, it goes through so many stages. And when it comes to security, it is crucial to ensure security precautions at all levels. We would like to describe some great security practices that mobile developers follow these days.
Consider all possible risks
Before the development of your app starts, the team of technicians spends some time analyzing the risks. It is important to predict what and how exactly something can harm your app and decide beforehand how the application will handle sensitive data, utilize payment credentials, PIN codes, passwords or else.
One more crucial step is the selection of the right API and safe library for your future solution. And last but not least, whatever solution you are developing, it should follow key industrial guidelines and be compliant with the industry standards. For example, if your mobile app works with sensitive data, then it should be GDPR compliant and have all necessary documentation to prove it.
Follow iOS and Android guidelines
You may think that your app is well protected, and yet you should not forget to check all the existing security guidelines provided for iOS and Android. Those guidelines include information about preferable security configurations, right permissions that should be requested, proper authorization and encryption procedures, etc.
Perform code obfuscation
It is a well-known practice when developers use code obfuscation to protect mobile solutions from hacker attacks. Code obfuscation includes encryption of some code elements or the entire code. Then comes metadata removal so that the information about libraries of APIs cannot be easily accessed. And finally, the renaming of classes and variables is performed. Take a look at this picture comparing a common code with obfuscated one:
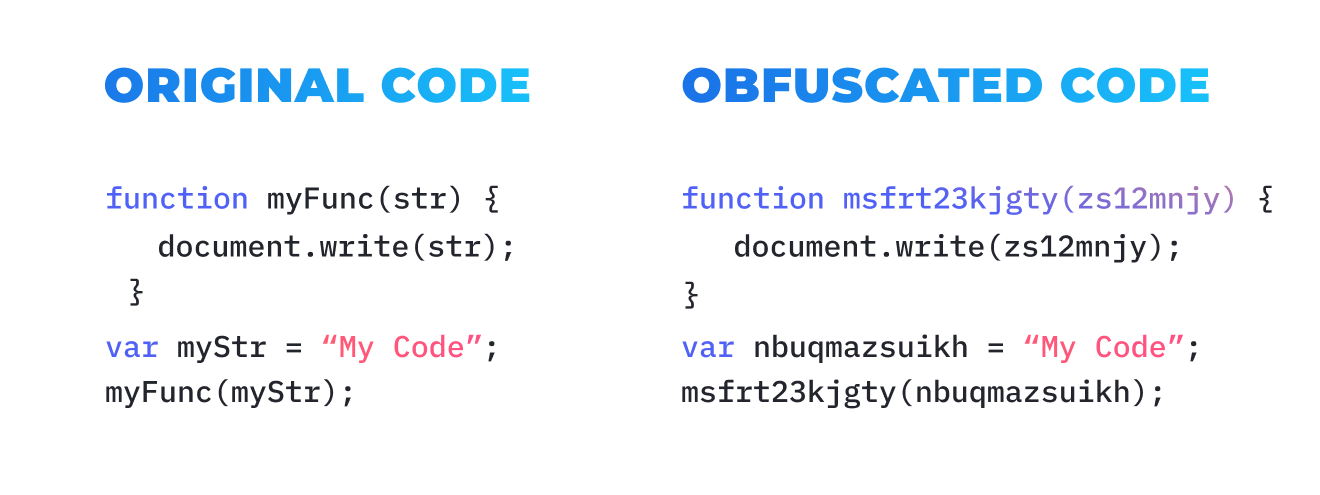
All of the actions we mentioned above help convert the code into a format that a human cannot read. Code obfuscation is widely used by Android developers since, unlike iOS, Android has open-source libraries.
Test your app from time to time
It is impossible to make your mobile app secure once and for all. Each year hackers become more inventive and equipped with more sophisticated tools attacking the apps. New threats can emerge every day, and you need to be prepared to target them quickly and patch them before any real damage is made.
To be able to do this, you simply need to test your mobile app from time to time. Penetration testing is also a must – it helps to find all potential app weaknesses and check if there is any unencrypted data, password expiry protocols, or maybe suspicious permissions granted to third-party services. Here at Altamira, we offer holistic post-release maintenance, so that you can benefit from our services and be sure that your app will be properly tested and improved if needed.
Enforce sessions logout
Almost all business and customer-centered mobile applications work with payment processing, and sometimes common users forget to logout in the end. Such obscurity can lead to severe consequences, therefore it is a good practice to enforce session logouts in mobile applications that deal with banking transactions. This great security measure is already used by many online banking apps.
Best mobile security practices Altamira uses
During the course of ten years, Altmaira has developed numerous mobile applications for different businesses. We built online banking apps, social networks, dating apps, trading and betting solutions, apps for education, work, entertainment, and many more. And of course, while building each of these applications, we prioritized their security.
Our approach to security is holistic. Before starting the development of a mobile application, we carefully assess potential weaknesses and how we can possibly handle them. Our developers explore such well-known mobile threats as ransomware, spyware, adware, fraud tools, various vulnerability types that iOS and Android solutions have, and many other additional security-related matters.
Also, our software engineers revise MASVS (mobile application security verification standards) that contain all of the following requirements:
- Architecture, design and threat modeling;
- Data storage and privacy;
- Authentication and session management;
- Network communication;
- Platform and integrations interaction;
- Code quality;
- App resilience.
Having all information and requirements at our hands, we also explore mandatory industrial standards and compliances to build a solution that meets them. We protect mobile solutions from data leaks, perform logging, encrypt all data and traffic, and keep an eye on main files storages. We always select up-to-date libraries and secure third-party services for every mobile app.
So to cut it short, we ensure security at the level of coding and then at the level of testing. Our quality assurance specialists always perform a full audit of the requirements and complete all kinds of security assessments in accordance with OWASP. We have both manual and automated testing experts who make sure that your app is free of bugs and security loopholes.
What’s also great about Altamira experts is that you can be sure that no important security aspect is forgotten with us. We have special security checklists created by our experts. Those checklists contain all requirements that the app should be able to meet, key step-by-step actions, and expected results. Here is a snapshot demonstrating one of our checklists:
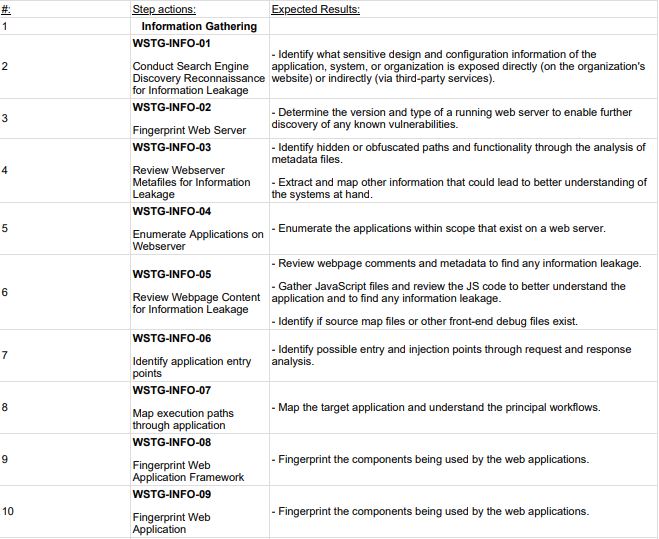
By choosing our team to develop your custom mobile application, you can be sure that you will end up with high-quality code, trendy and user-friendly design, and of course high level of security. We offer custom mobile app development services based on your business needs. And here is the technology stack that we use:
FAQ
Wrapping up
The importance of mobile app security should not be underestimated. After all, you need to take care not only of data safety but also about your brand reputation. Data breaches, security holes, and hacker attacks can lead to serious consequences. You can lose a lot of money, loyal clients and then spend many months on recovering your app and company reputation on the market. And you definitely do not need that.
So when you initiate custom mobile app development, stay focused not only on the functional and non-functional requirements, but on the app security as well. Choose a development team that uses the best security practices, follows mobile security guidelines and double-checks every single detail before releasing your app.






